| Age | Commit message (Collapse) | Author |
|---|
|
|
|
memory increase
|
|
5a1f57646b qa: clean up assert_memory_usage_stable utility (James O'Beirne)
0cf1632f03 qa: fix p2p_invalid_messages on macOS (James O'Beirne)
Pull request description:
Infinite mea culpa for the number of problems with this test.
This change bumps the acceptable RSS increase threshold from 3% to 50% when spamming the test node with junk 4MB messages. On [@MarcoFalke's macOS test build](https://travis-ci.org/MarcoFalke/btc_nightly) we see RSS grow ~14% from ~71MB to 81MB, so a 50% increase threshold should be more than sufficient to avoid spurious failures.
Tree-SHA512: 150a7b88080fd883c7a5d0b9ffa470f61a97c4885fccc1a06fde6260aaef15640a7c1de7e89c581b245df7807d617ec3d86775330386ec5149ad567492fc5d31
|
|
|
|
|
|
848077f94d clarify RPC rawtransaction documentation (Jameson Lopp)
Pull request description:
Fixing an RPC documentation typo and clarifying the wording of the testmempoolaccept function.
Tree-SHA512: 495c05ba322d0747ff569d02f5d2ad7d94b5542049c82091f5e74d8d02a8af408f31e10b112ca20d506125e3b39703ec3169f3a446f09ecae3cd46148ffc4041
|
|
|
|
e4eee7d09d Add Benchmark to test input de-duplication worst case (Jeremy Rubin)
Pull request description:
Because there are now 2PRs referencing this benchmark commit, we may as well add it independently as it is worth landing the benchmark even if neither patch is accepted.
https://github.com/bitcoin/bitcoin/pull/14397
https://github.com/bitcoin/bitcoin/pull/14387
Tree-SHA512: 4d947323c02297b0d8f5871f9e7cc42488c0e1792a8b10dc174a25f4dd53da8146fd276949a5dbacf4083f0c6a7235cb6f21a8bc35caa499bc2508f8a048b987
|
|
Fix nits
replace utiltime?
|
|
af9a9918b2 Fix detection of copyright holders (Cornelius Schumacher)
Pull request description:
Fix copyright holder detection so that `copyright_header.py report` creates a clean and accurate report:
* Fix list of copyright holders in the code
* Also detect copyrights which have a comma after the date
* Exclude directories which are git subtrees
Tree-SHA512: 7ab78618aa62c7d40b6688ddcde4a85c6fc5df8275271fa85518e146c1db90760bfafaa6036b9f6afbe887fd7e9274c913786101668573a3e289b3411aa6842f
|
|
* There is a copyright notice in `src/crypto/sha256_sse4.cpp` in the
middle of the file which contains a comma before the copyright
holder name. Correctly detect this so it's added to the report.
* Add missing copyright holders so that `copyright_header.py report`
doesn't show any unexpected copyright holder names anymore.
* Exclude files from git subtrees because they are maintained at the
original source.
|
|
fa7d36b8e7 test: Move UBSAN suppressions to test/sanitizer_suppressions/ubsan (MarcoFalke)
fa36d4e456 travis: --disable-hardening for xenial thread sanitizer (MarcoFalke)
89bf196c88 travis: Run thread sanitizer (MarcoFalke)
Pull request description:
On unit tests only for now. Disabled for the gui unit tests and all functional tests.
Tree-SHA512: 56f7d3b44e7cb68c76a2dc5abd85658955b1c2188932e988667c5a1cbcdd6be995d37bb949d62c6eb08a4aebfc43ff0370b7da1719d4e4f322a3495c1941a5e0
|
|
60ae463a68206b08faaadfbb023d7ede78fff784 Fix `bitcoin-qt -version` output formatting (Hennadii Stepanov)
Pull request description:
This PR makes command line output of `bitcoin-qt -version` formatted in the same way as `bitcoind -version` output.
Before:
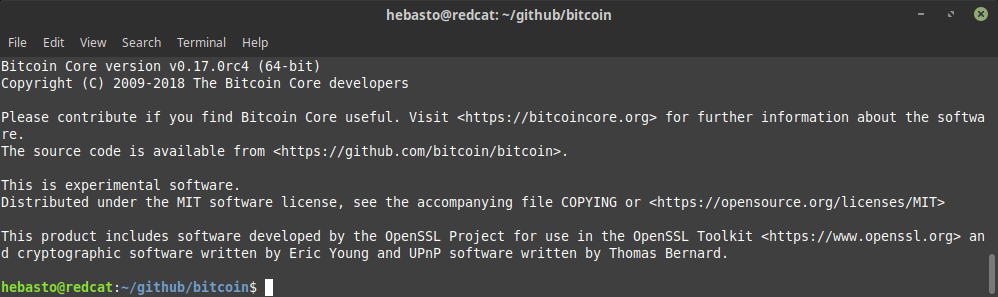
After:

Tree-SHA512: fd8bd20e2108b9562bcbf6c094f950e867a5755994e8acc28b07e52fe73d04f783201c20bde47be2083ce89fb3ef9749f9c3757d479ad6c48ed09c633155f47e
|
|
in CreateSig
b81a1860561ccbda3cd6913f54e49fdc91c7718c GetPubKey: make sigdata const (Gregory Sanders)
f7beb95a1f921ed292680fbd2f042b4bac73bf59 remove redundant KeyOriginInfo access, already done in CreateSig (Gregory Sanders)
Pull request description:
This redundancy is confusing as it looks like pubkeyhashes are special in some way based on where it's called.
Tree-SHA512: a980b7c774c6d69322945227a2b156489fb1991ebf57fe6f26096d5f8047f246a133debc241b05af67810f604b040079add3ab3d30d9e2928095905a2afe17eb
|
|
75a4bf699fa6bdefa1b3d8cd405ea822d6ee01c0 Update release-process.md to include RC version bumping (Andrew Chow)
04b0bc7425e43de90856beeb1f33653db109fecd build: include rc number in version number (Andrew Chow)
895e6bbb2241e9175463734f3677398a9f38f0f8 build: if VERSION_BUILD is non-zero, include it in the package version (Andrew Chow)
Pull request description:
As noted on IRC, the filenames of the gitian build results do not contain the 4th digit of the version number if it has one, e.g. 0.17.0.1 produces files with the number 0.17.0. Furthermore, when RC's are built, the resulting filenames are of the release version and do not include `rc` in them. This occurs because `configure.ac` is written to create version numbers of the form `major.minor.rev` instead of `major.minor.rev.build` and without any rc version as it does not handle rc numbers.
This PR changes `configure.ac` to include the build number if it is greater than 0. It will also include the rc number if it is greater than 0. So the filenames of the gitian builds will now contain the full version number.
This behavior can be tested by setting `_CLIENT_VERSION_BUILD` and `_CLIENT_VERSION_RC` to non-zero values and then doing `make dist`. A tar file should be created with the correct versioning.
Tree-SHA512: b77990485f2c7770be897dc136737cd805306afff9882ebef7170741f363203587356ccf8bec83163268ace1bd77433fbd2ba8c213f993677bfb867d99a0bbe7
|
|
0c69ff61719e9bc4938a9675a36b4170dfca4e6c clarify rpcwallet flag url change (Jordan Baczuk)
Pull request description:
This adds clarification to the bitcoin-cli -rpcwallet flag in the help command. This will benefit users who want to utilize this feature without the cli, for example curl. It isn't readily apparent that this changes the url used in the RPC call.
Tree-SHA512: 6fc759f193f0a918884aab8ba4dc77ed9e89ee3840feeff737a754be758750590f5bd44b40f4810c3b82601e125e62e10360af45cb8e9d95be206ebeb9120ebf
|
|
b7b36decaf878a8c1dcfdb4a27196c730043474b fix uninitialized read when stringifying an addrLocal (Kaz Wesley)
8ebbef016928811756e46b9086067d1c826797a8 add test demonstrating addrLocal UB (Kaz Wesley)
Pull request description:
Reachable from either place where SetIP is used when all of:
- our best-guess addrLocal for a peer is IPv4
- the peer tells us it's reaching us at an IPv6 address
- NET logging is enabled
In that case, SetIP turns an IPv4 address into an IPv6 address without
setting the scopeId, which is subsequently read in GetSockAddr during
CNetAddr::ToStringIP and passed to getnameinfo. Fix by ensuring every
constructor initializes the scopeId field with something.
Tree-SHA512: 8f0159750995e08b985335ccf60a273ebd09003990bcf2c3838b550ed8dc2659552ac7611650e6dd8e29d786fe52ed57674f5880f2e18dc594a7a863134739e3
|
|
fa5e0452e875a7ca6bf6fe61fdd652d341eece40 rpc: Documentation fixups (MarcoFalke)
fa91e8eda541acdb78ca481b74605639f319c108 Use RPCHelpMan for all RPCs (MarcoFalke)
fa520e72f7b5964cea1ade666e71212914556cf3 lint: Must use RPCHelpMan to generate the RPC docs (MarcoFalke)
Pull request description:
The resulting documentation should not change unless the type in the oneline-summary was previously incorrect. (E.g. string vs bool)
Tree-SHA512: 4ff355b6a53178f02781e97a7aca7ee1d0d97ff348b6bf5a01caa1c96904ee33c704465fae54c2cd7445097427fd04c71ad3779bb7a7ed886055ef36c1b5a1d0
|
|
8284756705dc05ef2e5a6bdfeab146d3cebe35ca A few minor formatting fixes and clarifications to descriptors.md (John Newbery)
Pull request description:
Fixes some markdown formatting issues, and also adds a few clarifications.
Tree-SHA512: b12fc94035c075a990756e22fb60b95e6c851c80c8a60fc8fc46b07c6749df4d257401889be4d930996432ac08850770077e667fe48473140f38b94c8e9eacdc
|
|
3d2c7d6f94 Add regtest for JSON-RPC batch calls. (Daniel Kraft)
Pull request description:
This adds a new regtest file `interface_rpc.py`, containing a test for batch JSON-RPC requests. Those were previously not tested at all. Tests for basic requests are not really necessary, as those are used anyway in lots of other regtests.
The existing `interface_http.py` file is more about the underlying HTTP connection, so adding a new interface file for the JSON-RPC specific things makes sense.
Tree-SHA512: 7c7576004c8474e23c98f4bf25fb655328ba6bb73ea06744ebee1c0ffbb26bc132e621ae52955d51dab0803b322f8d711667626a777ac9b26003339c2484502f
|
|
|
|
https://gcc.gnu.org/bugzilla/show_bug.cgi?id=67308
|
|
|
|
fa21ca09a8 test: Add BOOST_REQUIRE to getters returning optional (MarcoFalke)
Pull request description:
Usually the returned value is already checked for equality, but for sanity we might as well require that the getter successfully returned.
Tree-SHA512: 0d613a9a721c61bd7a115ebc681a0890df09b8e5775f176ac18b3a586f2ca57bee0b5b816f5a7c314ff3ac6cbb2a4d9c434f8459e054a7c8a6934a75f0120c2a
|
|
d6cde007db9d3e6ee93bd98a9bbfdce9bfa9b15b rpcauth: Improve by using argparse and getpass modules (João Barbosa)
Pull request description:
This PR improves argument handling in `rpcauth.py` script by using `argparse` module. Specifying `-` as password makes it prompt securely with `getpass` module which prevents leaking passwords to bash history.
Tree-SHA512: 489d66c95f66b5618cb75fd8f07ea5647281226ab9e32b03051eb43f758b9334ac19b7c82c2ed4f8c7ffbb0bee949b3d389e1564ec7a6e372f2864233bc7cb88
|
|
explicitly
27c44ef9c61f64d941ab82ec232a68141a2fde90 rpcbind: Warn about exposing RPC to untrusted networks (Luke Dashjr)
d6a1287481428d982dc03be3a6d9aeef8398f468 CNetAddr: Add IsBindAny method to check for INADDR_ANY (Luke Dashjr)
3615003952ffbc814bdb53d9d0e45790f152bd2f net: Always default rpcbind to localhost, never "all interfaces" (Luke Dashjr)
Pull request description:
A disturbingly large number of listening nodes appear to be also exposing their RPC server to the public internet. To attempt to mitigate this:
* Only ever bind localhost by default, even if `rpcallowip` is specified. (A warning is given if `rpcallowip` is specified without `rpcbind`, since it doesn't really make sense to do.)
* Warn about exposing the RPC server to untrusted networks if the user explicitly binds to any INADDR_ANY address.
* Include a warning about untrusted networks in the `--help` documentation for `rpcbind`.
Tree-SHA512: 755bbca3db416a31393672eccf6675a5ee4d1eb1812cba73ebb4ff8c6b855ecc5df4c692566e9aa7b0f7d4dce6fedb9c0e9f3c265b9663aca36c4a6ba5efdbd4
|
|
69ca48717ceb31e37e90276278362c809cf98cc6 Implement prevector::fill once (Ben Woosley)
7bad78c2c83d73b7e0518f3e1b835f0157b80ec6 Drop defunct IS_TRIVIALLY_CONSTRUCTIBLE handling from prevector.h (Ben Woosley)
Pull request description:
This is clean-up post #14651:
* Use one implementation of `prevector::fill`, as it's possible now that the implementations are identical.
* Only apply the `IS_TRIVIALLY_CONSTRUCTIBLE` handling to the bench file where it is used, and drop the now-unnecessary associated compat includes.
Tree-SHA512: 5930b3a17fccd39af10add40202ad97a297aebecc049af72ca920d0d55b3e4c3c30ce864c8a683355895f0196396d4ea56ba9f9637bdc7d16964cdf66c195485
|
|
|
|
|
|
|
|
We don't support binding to untrusted networks, so avoid a default where that is typical
|
|
|
|
This adds a new regtest file 'interface_rpc.py', containing a test for
batch JSON-RPC requests. Those were previously not tested at all. Tests
for basic requests are not really necessary, as those are used anyway
in lots of other regtests.
The existing interface_http.py file is more about the underlying HTTP
connection, so adding a new interface file for the JSON-RPC specific
things makes sense.
|
|
3fb09b9889665a24b34f25e9d1385a05058a28b7 Warn unrecognized sections in the config file (Akio Nakamura)
Pull request description:
This PR intends to resolve #14702.
In the config file, sections are specified by square bracket pair "[]"$,
or included in the option name itself which separated by a period"(.)".
Typicaly, [testnet] is not a correct section name and specified options
in that section are ignored but user cannot recognize what is happen.
So, add some log-warning messages if unrecognized section names are
present in the config file after checking section only args.
note: Currentry, followings are out of scope of this PR.
1) Empty section name or option name can describe.
e.g. [] , .a=b, =c
2) Multiple period characters can exist in the section name and option name.
e.g. [c.d.e], [..], f.g.h.i=j, ..=k
Tree-SHA512: 2cea02a0525feb40320613989a75cd7b7b1bd12158d5e6f3174ca77e6a25bb84425dd8812f62483df9fc482045c7b5402d69bc714430518b1847d055a2dc304b
|
|
fa7da0617c814aeb06d5c70c4bb8e18c79fb8725 qa: Check specific reject reasons in feature_block (MarcoFalke)
Pull request description:
There are some consensus checks that are essentially turned off because we never send the block, but only the header. It happens that the header was sufficient to determine the invalidity of the block according to our consensus rules in those cases. Fix that by forcing the full block on the node unsolicited.
Tree-SHA512: a5534318370367ea8de07d853de7e845c8f5637cd6d5457e932a9555af26cc212625e443c00c93586d556cc770f301248e7cabd68131a37791ae91706e7e40b2
|
|
6be7d14d243eeeaaf6b4b98c3359c3e1695f2046 Properly generate salt in rpcauth.py, update tests (Carl Dong)
Pull request description:
Previously, when iterating over bytes of the generated salt to construct
a hex string, only one character would be outputted when the byte is
less than 0x10. Meaning that for a 16 byte salt, the hex string might be
less than 32 characters and collisions would occur.
Tree-SHA512: 7038ecbbac846cd1851112396acd8a04475685f5b6f786e4e7316acba4a56cc711c275b7f52f0f2b6bc6cfdc0c0d9d39c3afeb2c0aff3a30fde516bf642fdf9f
|
|
|
|
feeef7d30ed7372d1941a2f2a54669f5b9309cf2 Do not specify sudo in .travis (Julian Fleischer)
Pull request description:
Travis is deprecating the `sudo` keyword and moves everything to
the same infrastructure (sudo really selects between two infrastructures).
See https://blog.travis-ci.com/2018-11-19-required-linux-infrastructure-migration?utm_source=in-app&utm_medium=intercom for more info.
Tree-SHA512: 3364fbeaf7af5e91ef97cf7fbcc75427ecb4e10b02a31cbc17ccc46a6077bba7a000539717bb6a351c404a2b408af7de6c4587089b02367e67e1c8bfd8fe69d1
|
|
Travis is deprecating the `sudo` keyword and moves everything to
the same infrastructure (sudo really selects between two infrastructures).
See https://blog.travis-ci.com/2018-11-19-required-linux-infrastructure-migration?utm_source=in-app&utm_medium=intercom for more info.
|
|
591203149f1700f594f781862e88cbbfe83d8d37 wallet: Create IsDatabaseLoaded function (Chun Kuan Lee)
15c93f075a881deb3ad7b1dd8a4516a9b06e5e11 wallet: Add trailing wallet.dat when detecting duplicate wallet if it's a directory. (Chun Kuan Lee)
c456fbd8dfcc748e5ec9feaa57ec0f2900f99cde Refactor: Move m_db pointers into BerkeleyDatabase (Russell Yanofsky)
Pull request description:
Fix #14538
Fix crash attempting to load the same wallet with different path strings that resolve to the same absolute path. The primary check which prevents loading the same wallet twice is:
https://github.com/bitcoin/bitcoin/blob/6b8d0a2164b30eab76e7bccb1ffb056a10fba406/src/wallet/db.cpp#L44
But this check is skipped if both wallet paths resolve to the same absolute path, due to caching here:
https://github.com/bitcoin/bitcoin/blob/6b8d0a2164b30eab76e7bccb1ffb056a10fba406/src/wallet/db.cpp#L467
Meanwhile a secondary check for duplicate wallets is not reliable because it based on a literal comparison, instead of comparison using absolute paths:
https://github.com/bitcoin/bitcoin/blob/6b8d0a2164b30eab76e7bccb1ffb056a10fba406/src/wallet/wallet.cpp#L3853
This PR fixes the latter check to compare the absolute path of a new wallet being loaded to absolute paths of wallets already loaded, so there should no longer be any way to load the same wallet more than once.
Tree-SHA512: 2fa01811c160b57be3b76c6b4983556a04bbce71a3f8202429987ec020664a062e897deedcd9248bc04e9baaa2fc7b464e2595dcaeff2af0818387bf1fcdbf6f
|
|
In the config file, sections are specified by square bracket pair "[]"$,
or included in the option name itself which separated by a period"(.)".
Typicaly, [testnet] is not a correct section name and specified options
in that section are ignored but user cannot recognize what is happen.
So, add some log/stderr-warning messages if unrecognized section names
are present in the config file after checking section only args.
|
|
e816b341ab794fb84d89efb90b8c0f369d34d6ca revert removal of fstream.hpp header in fs.h (Karl-Johan Alm)
Pull request description:
We cannot (yet) remove the EXPECTED_BOOST_INCLUDES entry as this header is still needed in `fs.h` (see #14763).
Partially reverts #14718.
Tree-SHA512: e94d8d6208bee14af20a7a529e60a4898358ec8c070a8bf0701e589a2ae33df1305deac83cee619f103c24be0eb3c12a2f490209c125b247acf21561c7de456e
|
|
This is required for some architectures.
|
|
c54e5a41c4 Remove unreferenced boost headers (Murray Nesbitt)
Pull request description:
Building with clang (e.g. on FreeBSD) is very noisy due to `-Wthread-safety-analysis` warnings regarding boost. This change removes a number of unnecessary boost includes, and silences the rest of the warnings when building with clang. This allows more potentially interesting warnings to surface from the noise.
Tested on FreeBSD 11.2
Tree-SHA512: 5e6a0623188b9be59aeae52866799aefb4c3c9ab5e569b07ee8d43fc92e0b5f1f76b96bb54c35c7043148df84641b4a96927fb71f6eb00460c20cd19cf250900
|
|
b08af10fb299dc3fdcd1f022619fb112c72e5d8e disallow oversized CBlockHeaderAndShortTxIDs (Kaz Wesley)
6bed4b374daf26233e96fa7863d4324a5bfa99c2 fix a deserialization overflow edge case (Kaz Wesley)
051faf7e9d4e32142f95f7adb31d2f53f656cb66 add a test demonstrating an overflow in a deserialization edge case (Kaz Wesley)
Pull request description:
A specially-constructed BlockTransactionsRequest can cause `offset` to wrap in deserialization. In the current code, there is not any way this could be dangerous; but disallowing it reduces the potential for future surprises.
Tree-SHA512: 1aaf7636e0801a905ed8807d0d1762132ac8b4421a600c35fb6d5e5033c6bfb587d8668cd9f48c7a08a2ae793a677b7649661e3ae248ab4f8499ab7b6ede483c
|
|
Previously, when iterating over bytes of the generated salt to construct
a hex string, only one character would be outputted when the byte is
less than 0x10. Meaning that for a 16 byte salt, the hex string might be
less than 32 characters and collisions would occur.
|
|
07e286d940 Improve scripted-diff developer docs (Carl Dong)
Pull request description:
Instead of verifying all scripted-diffs, provide an example that only verifies all scripted-diffs in commits since `origin/master`.
Tree-SHA512: 2faecfd1df04046c77ca2b7426675265f7ed656b2b7e2714ae61c0a38b3ea239f35d2be6d615c5191a21f3a453e37f6a4622bd4558173b768cb73183b56c4d62
|
|
|
|
Instead of verifying all scripted-diffs, provide an example that only verifies all scripted-diffs in commits since `origin/master.
|
|
Reachable from either place where SetIP is used when our best-guess
addrLocal for a peer is IPv4, but the peer tells us it's reaching us at
an IPv6 address.
In that case, SetIP turns an IPv4 address into an IPv6 address without
setting the scopeId, which is subsequently read in GetSockAddr during
CNetAddr::ToStringIP and passed to getnameinfo. Fix by ensuring every
constructor initializes the scopeId field with something.
|
