diff options
| author | W. J. van der Laan <laanwj@protonmail.com> | 2021-06-03 18:19:11 +0200 |
|---|---|---|
| committer | W. J. van der Laan <laanwj@protonmail.com> | 2021-06-03 18:43:55 +0200 |
| commit | 07ededa30c9473ac32fc3e12b399c0ba999a4c40 (patch) | |
| tree | 03d8fb170199f3c2bf0c79a048146e1d37a5b0d7 /src/test | |
| parent | 907d636e5e76bd884a4ca1a1ebd8db68a3e64705 (diff) | |
| parent | 5d82a57db4f67506a4e80d186ba76f3a8665e147 (diff) | |
Merge bitcoin/bitcoin#22050: p2p: remove tor v2 support
5d82a57db4f67506a4e80d186ba76f3a8665e147 contrib: remove torv2 seed nodes (Jon Atack)
5f7e086dac78c9070f8292a1757d7e77e110f772 contrib: update generate-seeds.py to ignore torv2 addresses (Jon Atack)
8be56f0f8ecc54744d572e5678a3089665587b98 p2p, refactor: extract OnionToString() from CNetAddr::ToStringIp() (Jon Atack)
5f9d3c09b4c9cd026cdc7c3a81f91632280917b7 p2p: remove torv2 from CNetAddr::ToStringIP() (Jon Atack)
3d390421440f1cae9a9f2b089561c183ecd1b073 p2p: remove torv2 in SetIP() and ADDR_TORV2_SIZE constant (Jon Atack)
cff5ec477a388ae9aa9fd9ef6a7dad1f678e7d23 p2p: remove pre-addrv2 onions from SerializeV1Array() (Jon Atack)
4192a74413907717d6173e393724b931f2225dd9 p2p: ignore torv2-in-ipv6 addresses in SetLegacyIPv6() (Jon Atack)
1d631e956fffbbc7891ed40be4fd39aeff036c52 p2p: remove BIP155Network::TORV2 from GetBIP155Network() (Jon Atack)
7d1769bc450a98c093a066d6daed84337040dbfb p2p: remove torv2 from SetNetFromBIP155Network() (Jon Atack)
eba9a94b9f56be2fda623e77f19b960425ea1eb5 fuzz: rename CNetAddr/CService deserialize targets (Jon Atack)
c56a1c9b182815018b8bd3d8e6b8c2cb27859607 p2p: drop onions from IsAddrV1Compatible(), no longer relay torv2 (Jon Atack)
f8e94002fcfdc7890d38c23488b1f3a662e97bc4 p2p: remove torv2/ADDR_TORV2_SIZE from SetTor() (Jon Atack)
0f1c58ae87d6a3fe81816500e7b8275420d151d0 test: update feature_proxy to torv3 (Jon Atack)
Pull request description:

This patch removes support in Bitcoin Core for Tor v2 onions, which are already removed from the release of Tor 0.4.6.
- no longer serialize/deserialize and relay Tor v2 addresses
- ignore incoming Tor v2 addresses
- remove Tor v2 addresses from the addrman and peers.dat on node launch
- update generate-seeds.py to ignore Tor v2 addresses
- remove Tor v2 hard-coded seeds
Tested with tor-0.4.6.1-alpha (no v2 support) and 0.4.5.7 (v2 support). With the latest Tor (no v2 support), this removes all the warnings like those reported with current master in https://github.com/bitcoin/bitcoin/issues/21351
```
<bitcoind debug log>
Socks5() connect to […].onion:8333 failed: general failure
<tor log>
Invalid hostname [scrubbed]; rejecting
```
and the addrman no longer has Tor v2 addresses on launching bitcoind.
```rake
$ ./src/bitcoin-cli -addrinfo
{
"addresses_known": {
"ipv4": 44483,
"ipv6": 8467,
"torv2": 0,
"torv3": 2296,
"i2p": 6,
"total": 55252
}
}
```
After recompiling back to current master and restarting with either of the two Tor versions (0.4.5.7 or 0.4.6.1), -addrinfo initially returns 0 Tor v2 addresses and then begins finding them again.
Ran nodes on this patch over the past week on mainnet/testnet/signet/regtest after building with DEBUG_ADDRMAN.
Verified that this patch bootstraps an onlynet=onion node from the Tor v3 hardcoded fixed seeds on mainnet and testnet and connects to blocks and v3 onion peers: `rm ~/.bitcoin/testnet3/peers.dat ; ./src/bitcoind -testnet -dnsseed=0 -onlynet=onion`
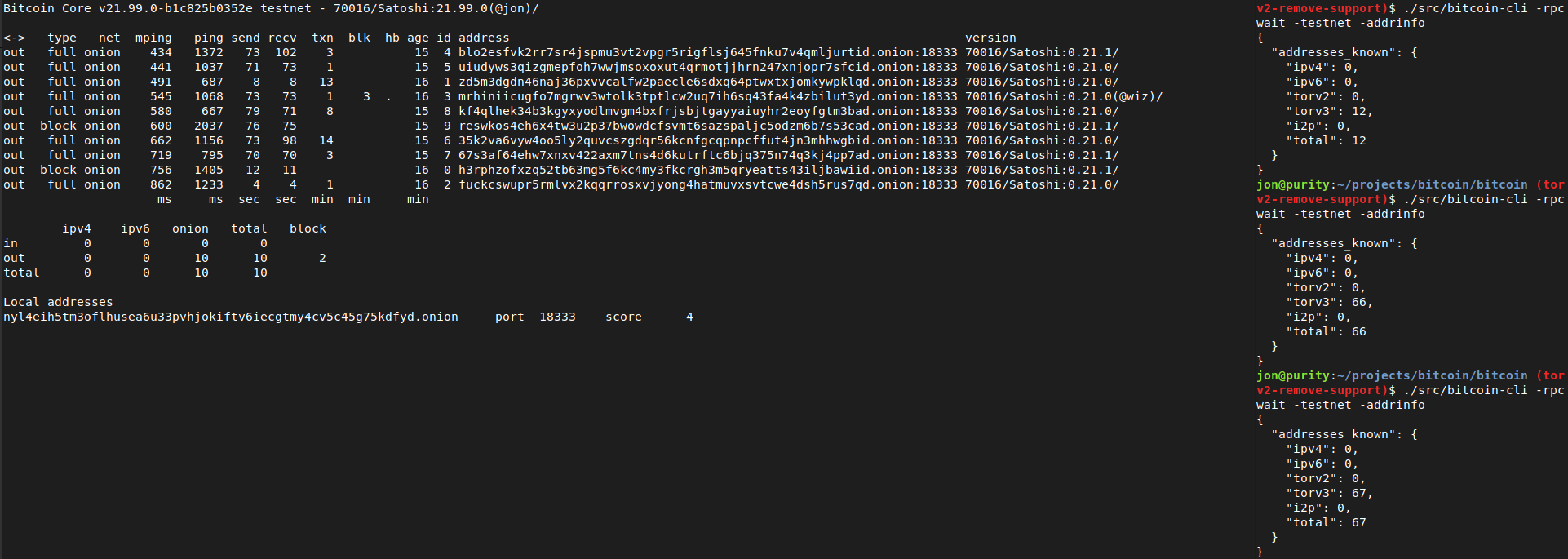
Tested using `addnode`, `getaddednodeinfo`,`addpeeraddress`, `disconnectnode` and `-addrinfo` that a currently valid, connectable Tor v2 peer can no longer be added:

Thanks to Vasil Dimov, Carl Dong, and Wladimir J. van der Laan for their work on BIP155 and Tor v3 that got us here.
ACKs for top commit:
laanwj:
Code review ACK 5d82a57db4f67506a4e80d186ba76f3a8665e147
Tree-SHA512: 590ff3d2f6ef682608596facb4b01f44fef69716d2ab3552ae1655aa225f4bf104f9ee08d6769abb9982a8031de93340df553279ce1f5023771f9f2b651178bb
Diffstat (limited to 'src/test')
| -rw-r--r-- | src/test/fuzz/deserialize.cpp | 6 | ||||
| -rw-r--r-- | src/test/net_tests.cpp | 39 | ||||
| -rw-r--r-- | src/test/netbase_tests.cpp | 36 |
3 files changed, 22 insertions, 59 deletions
diff --git a/src/test/fuzz/deserialize.cpp b/src/test/fuzz/deserialize.cpp index 1290c78712..700e368319 100644 --- a/src/test/fuzz/deserialize.cpp +++ b/src/test/fuzz/deserialize.cpp @@ -143,7 +143,7 @@ FUZZ_TARGET_DESERIALIZE(script_deserialize, { CScript script; DeserializeFromFuzzingInput(buffer, script); }) -FUZZ_TARGET_DESERIALIZE(sub_net_deserialize, { +FUZZ_TARGET_DESERIALIZE(subnet_deserialize, { CSubNet sub_net_1; DeserializeFromFuzzingInput(buffer, sub_net_1, INIT_PROTO_VERSION); AssertEqualAfterSerializeDeserialize(sub_net_1, INIT_PROTO_VERSION); @@ -223,7 +223,7 @@ FUZZ_TARGET_DESERIALIZE(coins_deserialize, { Coin coin; DeserializeFromFuzzingInput(buffer, coin); }) -FUZZ_TARGET_DESERIALIZE(netaddr_deserialize, { +FUZZ_TARGET_DESERIALIZE(net_address_deserialize, { CNetAddr na; DeserializeFromFuzzingInput(buffer, na); if (na.IsAddrV1Compatible()) { @@ -231,7 +231,7 @@ FUZZ_TARGET_DESERIALIZE(netaddr_deserialize, { } AssertEqualAfterSerializeDeserialize(na, INIT_PROTO_VERSION | ADDRV2_FORMAT); }) -FUZZ_TARGET_DESERIALIZE(service_deserialize, { +FUZZ_TARGET_DESERIALIZE(net_service_deserialize, { CService s; DeserializeFromFuzzingInput(buffer, s); if (s.IsAddrV1Compatible()) { diff --git a/src/test/net_tests.cpp b/src/test/net_tests.cpp index 7a122bd8b0..46f88c1282 100644 --- a/src/test/net_tests.cpp +++ b/src/test/net_tests.cpp @@ -318,15 +318,8 @@ BOOST_AUTO_TEST_CASE(cnetaddr_basic) BOOST_CHECK(!addr.IsBindAny()); BOOST_CHECK_EQUAL(addr.ToString(), link_local); - // TORv2 - BOOST_REQUIRE(addr.SetSpecial("6hzph5hv6337r6p2.onion")); - BOOST_REQUIRE(addr.IsValid()); - BOOST_REQUIRE(addr.IsTor()); - - BOOST_CHECK(!addr.IsI2P()); - BOOST_CHECK(!addr.IsBindAny()); - BOOST_CHECK(addr.IsAddrV1Compatible()); - BOOST_CHECK_EQUAL(addr.ToString(), "6hzph5hv6337r6p2.onion"); + // TORv2, no longer supported + BOOST_CHECK(!addr.SetSpecial("6hzph5hv6337r6p2.onion")); // TORv3 const char* torv3_addr = "pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion"; @@ -470,10 +463,8 @@ BOOST_AUTO_TEST_CASE(cnetaddr_serialize_v1) BOOST_CHECK_EQUAL(HexStr(s), "1a1b2a2b3a3b4a4b5a5b6a6b7a7b8a8b"); s.clear(); - BOOST_REQUIRE(addr.SetSpecial("6hzph5hv6337r6p2.onion")); - s << addr; - BOOST_CHECK_EQUAL(HexStr(s), "fd87d87eeb43f1f2f3f4f5f6f7f8f9fa"); - s.clear(); + // TORv2, no longer supported + BOOST_CHECK(!addr.SetSpecial("6hzph5hv6337r6p2.onion")); BOOST_REQUIRE(addr.SetSpecial("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion")); s << addr; @@ -508,10 +499,8 @@ BOOST_AUTO_TEST_CASE(cnetaddr_serialize_v2) BOOST_CHECK_EQUAL(HexStr(s), "02101a1b2a2b3a3b4a4b5a5b6a6b7a7b8a8b"); s.clear(); - BOOST_REQUIRE(addr.SetSpecial("6hzph5hv6337r6p2.onion")); - s << addr; - BOOST_CHECK_EQUAL(HexStr(s), "030af1f2f3f4f5f6f7f8f9fa"); - s.clear(); + // TORv2, no longer supported + BOOST_CHECK(!addr.SetSpecial("6hzph5hv6337r6p2.onion")); BOOST_REQUIRE(addr.SetSpecial("kpgvmscirrdqpekbqjsvw5teanhatztpp2gl6eee4zkowvwfxwenqaid.onion")); s << addr; @@ -617,26 +606,14 @@ BOOST_AUTO_TEST_CASE(cnetaddr_unserialize_v2) BOOST_CHECK(!addr.IsValid()); BOOST_REQUIRE(s.empty()); - // Valid TORv2. + // TORv2, no longer supported. s << MakeSpan(ParseHex("03" // network type (TORv2) "0a" // address length "f1f2f3f4f5f6f7f8f9fa")); // address s >> addr; - BOOST_CHECK(addr.IsValid()); - BOOST_CHECK(addr.IsTor()); - BOOST_CHECK(addr.IsAddrV1Compatible()); - BOOST_CHECK_EQUAL(addr.ToString(), "6hzph5hv6337r6p2.onion"); + BOOST_CHECK(!addr.IsValid()); BOOST_REQUIRE(s.empty()); - // Invalid TORv2, with bogus length. - s << MakeSpan(ParseHex("03" // network type (TORv2) - "07" // address length - "00")); // address - BOOST_CHECK_EXCEPTION(s >> addr, std::ios_base::failure, - HasReason("BIP155 TORv2 address with length 7 (should be 10)")); - BOOST_REQUIRE(!s.empty()); // The stream is not consumed on invalid input. - s.clear(); - // Valid TORv3. s << MakeSpan(ParseHex("04" // network type (TORv3) "20" // address length diff --git a/src/test/netbase_tests.cpp b/src/test/netbase_tests.cpp index 3c47cf83e2..687d2f6747 100644 --- a/src/test/netbase_tests.cpp +++ b/src/test/netbase_tests.cpp @@ -44,13 +44,12 @@ static CNetAddr CreateInternal(const std::string& host) BOOST_AUTO_TEST_CASE(netbase_networks) { - BOOST_CHECK(ResolveIP("127.0.0.1").GetNetwork() == NET_UNROUTABLE); - BOOST_CHECK(ResolveIP("::1").GetNetwork() == NET_UNROUTABLE); - BOOST_CHECK(ResolveIP("8.8.8.8").GetNetwork() == NET_IPV4); - BOOST_CHECK(ResolveIP("2001::8888").GetNetwork() == NET_IPV6); - BOOST_CHECK(ResolveIP("FD87:D87E:EB43:edb1:8e4:3588:e546:35ca").GetNetwork() == NET_ONION); - BOOST_CHECK(CreateInternal("foo.com").GetNetwork() == NET_INTERNAL); - + BOOST_CHECK(ResolveIP("127.0.0.1").GetNetwork() == NET_UNROUTABLE); + BOOST_CHECK(ResolveIP("::1").GetNetwork() == NET_UNROUTABLE); + BOOST_CHECK(ResolveIP("8.8.8.8").GetNetwork() == NET_IPV4); + BOOST_CHECK(ResolveIP("2001::8888").GetNetwork() == NET_IPV6); + BOOST_CHECK(ResolveIP("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion").GetNetwork() == NET_ONION); + BOOST_CHECK(CreateInternal("foo.com").GetNetwork() == NET_INTERNAL); } BOOST_AUTO_TEST_CASE(netbase_properties) @@ -73,7 +72,7 @@ BOOST_AUTO_TEST_CASE(netbase_properties) BOOST_CHECK(ResolveIP("2001:20::").IsRFC7343()); BOOST_CHECK(ResolveIP("FE80::").IsRFC4862()); BOOST_CHECK(ResolveIP("64:FF9B::").IsRFC6052()); - BOOST_CHECK(ResolveIP("FD87:D87E:EB43:edb1:8e4:3588:e546:35ca").IsTor()); + BOOST_CHECK(ResolveIP("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion").IsTor()); BOOST_CHECK(ResolveIP("127.0.0.1").IsLocal()); BOOST_CHECK(ResolveIP("::1").IsLocal()); BOOST_CHECK(ResolveIP("8.8.8.8").IsRoutable()); @@ -133,18 +132,6 @@ BOOST_AUTO_TEST_CASE(netbase_lookupnumeric) BOOST_CHECK(TestParse("[fd6c:88c0:8724:1:2:3:4:5]", "[fd6c:88c0:8724:1:2:3:4:5]:65535")); } -BOOST_AUTO_TEST_CASE(onioncat_test) -{ - // values from https://web.archive.org/web/20121122003543/http://www.cypherpunk.at/onioncat/wiki/OnionCat - CNetAddr addr1(ResolveIP("5wyqrzbvrdsumnok.onion")); - CNetAddr addr2(ResolveIP("FD87:D87E:EB43:edb1:8e4:3588:e546:35ca")); - BOOST_CHECK(addr1 == addr2); - BOOST_CHECK(addr1.IsTor()); - BOOST_CHECK(addr1.ToStringIP() == "5wyqrzbvrdsumnok.onion"); - BOOST_CHECK(addr1.IsRoutable()); - -} - BOOST_AUTO_TEST_CASE(embedded_test) { CNetAddr addr1(ResolveIP("1.2.3.4")); @@ -338,7 +325,6 @@ BOOST_AUTO_TEST_CASE(netbase_getgroup) BOOST_CHECK(ResolveIP("64:FF9B::102:304").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_IPV4, 1, 2})); // RFC6052 BOOST_CHECK(ResolveIP("2002:102:304:9999:9999:9999:9999:9999").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_IPV4, 1, 2})); // RFC3964 BOOST_CHECK(ResolveIP("2001:0:9999:9999:9999:9999:FEFD:FCFB").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_IPV4, 1, 2})); // RFC4380 - BOOST_CHECK(ResolveIP("FD87:D87E:EB43:edb1:8e4:3588:e546:35ca").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_ONION, 239})); // Tor BOOST_CHECK(ResolveIP("2001:470:abcd:9999:9999:9999:9999:9999").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_IPV6, 32, 1, 4, 112, 175})); //he.net BOOST_CHECK(ResolveIP("2001:2001:9999:9999:9999:9999:9999:9999").GetGroup(asmap) == std::vector<unsigned char>({(unsigned char)NET_IPV6, 32, 1, 32, 1})); //IPv6 @@ -481,10 +467,10 @@ BOOST_AUTO_TEST_CASE(netbase_dont_resolve_strings_with_embedded_nul_characters) BOOST_CHECK(!LookupSubNet("1.2.3.0/24\0"s, ret)); BOOST_CHECK(!LookupSubNet("1.2.3.0/24\0example.com"s, ret)); BOOST_CHECK(!LookupSubNet("1.2.3.0/24\0example.com\0"s, ret)); - BOOST_CHECK(LookupSubNet("5wyqrzbvrdsumnok.onion"s, ret)); - BOOST_CHECK(!LookupSubNet("5wyqrzbvrdsumnok.onion\0"s, ret)); - BOOST_CHECK(!LookupSubNet("5wyqrzbvrdsumnok.onion\0example.com"s, ret)); - BOOST_CHECK(!LookupSubNet("5wyqrzbvrdsumnok.onion\0example.com\0"s, ret)); + BOOST_CHECK(LookupSubNet("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion"s, ret)); + BOOST_CHECK(!LookupSubNet("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion\0"s, ret)); + BOOST_CHECK(!LookupSubNet("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion\0example.com"s, ret)); + BOOST_CHECK(!LookupSubNet("pg6mmjiyjmcrsslvykfwnntlaru7p5svn6y2ymmju6nubxndf4pscryd.onion\0example.com\0"s, ret)); } // Since CNetAddr (un)ser is tested separately in net_tests.cpp here we only |
